M-Sec Architecture
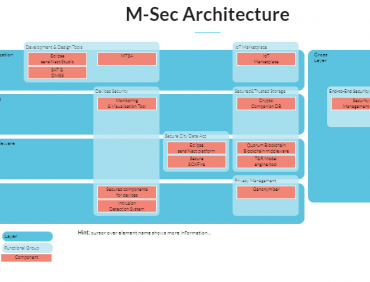
Simplified view of M-Sec architecture Application Layer Application layer defines all the use the IoT technology or in which IoT has deployed Eclipse sensiNact Studio Eclipse sensiNact Studio SensiNact is designed to allow platforms to interoperate, thus coexist and benefit from the richness of the variety. Additionally, it provides a fine grained security mechanism to […]